Firefox vs. Opera
I praise myself of having a rather complete overview of the browser market. On my main sytem, I've got Opera, Firefox, Seamonkey, Konqueror, and Midori. In virtual machines, I can test Iron or Chromium, as well as IE 8 and Safari, and compare builds of all browsers to each other on various OS.
Years ago, I wondered why everybody was using IE. There was no rational reason. People ... just were used to it.
Now, I have the feeling that we got the same situation with FF. People use it without even thinking. It's just assumed to be without alternative.
Personally, I almost exclusively use Opera. Why? Because Firefox is basically an open-source hypocrite. The Mozilla foundation promised a slim browser already seven years ago. What happened? We got a browser with zero functionality but the memory consumption of three mozillas. They also promised a transparent browser. And look what you got: about:config. 😄 Compare that to the oldfashioned ini files of Opera (and there's always about:opera for converts from FF 😉 ).
There is of course one feature of FF which is outstanding: it's add-on system. It's what makes FF unique, and distinguishes it from all other browsers. I would guess that 90% of its current users are not even aware of this feature, which is as much blessing as it's curse. Curse? Oh yes. It's a security concern of gigantic dimensions. Major updates break most add-ons. Many add-ons render the browser sluggish and unresponsive. Playing with add-ons is addictive. 😄 Blessing? Well, without add-ons FF is just as unusable as IE. But with the right add-ons you'll get a browser with impressive value.
Let's look at the list of FF add-ons I've installed. I've installed many of them to mimic a function of Opera. Those which aren't are possibly not that terribly important ... but they are fun. 😉 Oh, and one more thing: while Opera does not feature add-ons, it can still be customized to an amazing degree. There are user buttons, user scripts, user styles ... check it out here. Please understand that an NA entry (aka not available) in the table below simply means that I'm not aware of a realization via the above means.
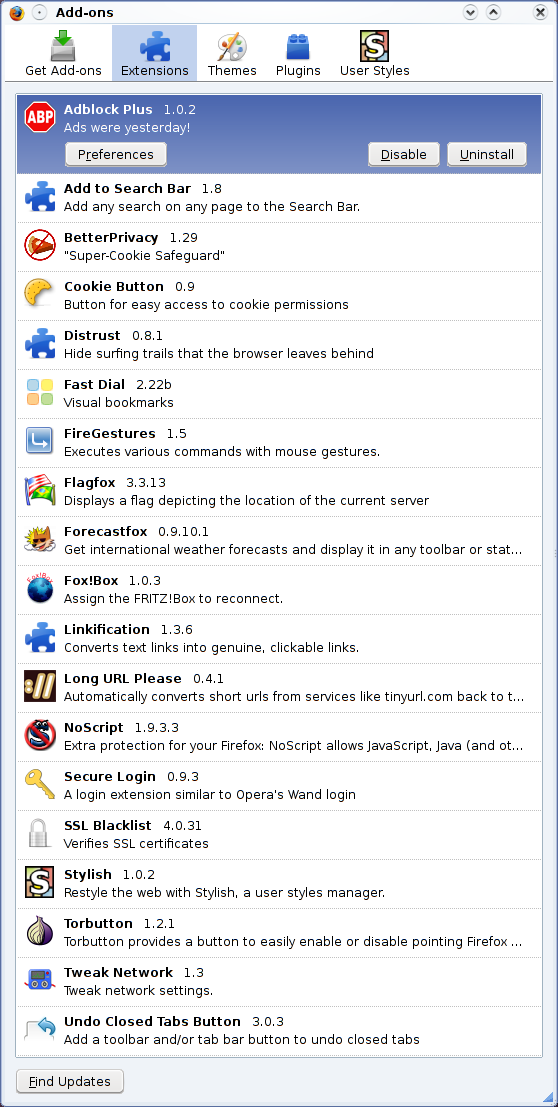
| Firefox
add-on |
Available in
Opera? |
| Adblock Plus |
built in (rightclick: block
content) [1] |
| Add to search bar |
built in (rightclick on search
box) |
| Better privacy |
NA |
| Cookie button |
built in (rightclick: site
preferences) |
| Distrust |
NA |
| Fast Dial |
built in (speed Dial) |
| Fire Gestures |
built in (mouse
gestures) |
| Flagfox |
NA |
| Forecastfox |
available as widget |
| Fox!Box! |
NA |
| Linkification |
rightclick, go to web
address |
| Long URL Please |
NA |
| No script |
built in (rightclick: site
preferences) |
| Secure login |
built in (Wand) |
| SSL blacklist |
NA |
| Stylish |
built in
(.opera/styles/user) |
| Torbutton |
available as Opera
button |
| Tweak network |
built in (preferences) |
| Undo Closed Tabs Buton |
built in (trash can) |
[1] A comprehensive urlfilter.ini, complete with a css for removing whitespace, and an adblocker realized as a user script.
Update: What a pity: Adsweep has been discontinued.