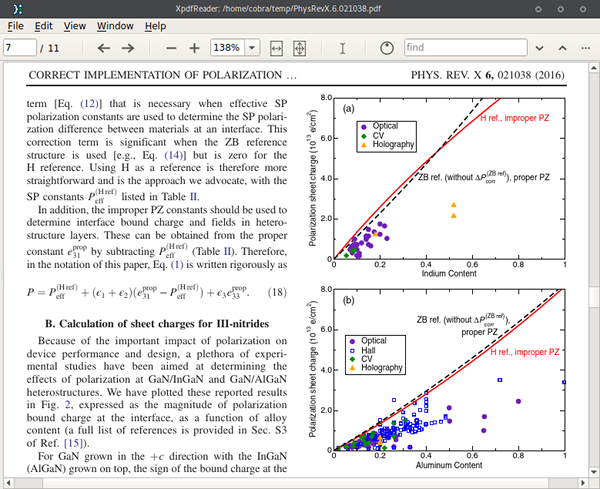
Intel microcode updates
Intel offers an updated microcode data file since 8th of January. According to Heise, these updates are exclusively devoted to Spectre and CPUs younger than 2013, Meltdown being taken care of by kernel updates, and older CPUs being (hopefully) the subject of subsequent microcode updates.
To examine and to eventually apply these updates, they have to be downloaded:
Arch:
sudo pacman -S intel-ucode
Debian:
sudo apt install intel-microcode
Debian automatically updates initrd, but for Arch, one has to update the bootlader as described in the wiki. Prior to doing so, one should check whether the updated microcode file actually holds updates for the CPU in use at all. In agreement with the report of Heise, there's no update for my Ivy Bridge Xeon:
➜ ~ bsdtar -Oxf /boot/intel-ucode.img | iucode_tool -tb -lS - iucode_tool: system has processor(s) with signature 0x000306a9 microcode bundle 1: (stdin) selected microcodes: 001/138: sig 0x000306a9, pf_mask 0x12, 2015-02-26, rev 0x001c, size 12288
But the Haswell i7 at work is destined to receive one:
➤ bsdtar -Oxf /boot/intel-ucode.img | iucode_tool -tb -lS - iucode_tool: system has processor(s) with signature 0x000306c3 microcode bundle 1: (stdin) selected microcodes: 001/147: sig 0x000306c3, pf_mask 0x32, 2017-11-20, rev 0x0023, size 23552
After a reboot, it is easy to ckeck whether an update of the microcode has taken place or not:
➜ ~ dmesg | grep microcode [ 0.000000] microcode: microcode updated early to revision 0x1c, date = 2015-02-26 [ 0.652031] microcode: sig=0x306a9, pf=0x2, revision=0x1c [ 0.652284] microcode: Microcode Update Driver: v2.2.
Same as before.
➤ dmesg | grep microcode [ 0.000000] microcode: microcode updated early to revision 0x23, date = 2017-11-20 [ 0.552077] microcode: sig=0x306c3, pf=0x2, revision=0x23 [ 0.552404] microcode: Microcode Update Driver: v2.2.
Indeed, a new one!
And what does the update do? Am I now immune to both Meltdown and Spectre on the Haswell system?
According to the 'Spectre & Meltdown Checker', the update has actually very little effect. Here's the result on my Xeon:
$ ./spectre-meltdown-checker.sh Spectre and Meltdown mitigation detection tool v0.29 Checking for vulnerabilities against running kernel Linux 4.14.13-1-ARCH #1 SMP PREEMPT Wed Jan 10 11:14:50 UTC 2018 x86_64 CPU is Intel(R) Xeon(R) CPU E3-1240 V2 @ 3.40GHz CVE-2017-5753 [bounds check bypass] aka 'Spectre Variant 1' - Checking count of LFENCE opcodes in kernel: NO > STATUS: VULNERABLE (only 21 opcodes found, should be >= 70, heuristic to be improved when official patches become available) CVE-2017-5715 [branch target injection] aka 'Spectre Variant 2' - Mitigation 1 - Hardware (CPU microcode) support for mitigation: NO - Kernel support for IBRS: NO - IBRS enabled for Kernel space: NO - IBRS enabled for User space: NO - Mitigation 2 - Kernel compiled with retpoline option: NO - Kernel compiled with a retpoline-aware compiler: NO > STATUS: VULNERABLE (IBRS hardware + kernel support OR kernel with retpoline are needed to mitigate the vulnerability) CVE-2017-5754 [rogue data cache load] aka 'Meltdown' aka 'Variant 3' - Kernel supports Page Table Isolation (PTI): YES - PTI enabled and active: YES > STATUS: NOT VULNERABLE (PTI mitigates the vulnerability)
And here's the Haswell. Note Spectre 2.
$ ./spectre-meltdown-checker.sh Spectre and Meltdown mitigation detection tool v0.29 Checking for vulnerabilities against running kernel Linux 4.14.13-1-ARCH #1 SMP PREEMPT Wed Jan 10 11:14:50 UTC 2018 x86_64 CPU is Intel(R) Core(TM) i7-4790 CPU @ 3.60GHz CVE-2017-5753 [bounds check bypass] aka 'Spectre Variant 1' - Checking count of LFENCE opcodes in kernel: NO > STATUS: VULNERABLE (only 21 opcodes found, should be >= 70, heuristic to be improved when official patches become available) CVE-2017-5715 [branch target injection] aka 'Spectre Variant 2' - Mitigation 1 - Hardware (CPU microcode) support for mitigation: YES - Kernel support for IBRS: NO - IBRS enabled for Kernel space: NO - IBRS enabled for User space: NO - Mitigation 2 - Kernel compiled with retpoline option: NO - Kernel compiled with a retpoline-aware compiler: NO > STATUS: VULNERABLE (IBRS hardware + kernel support OR kernel with retpoline are needed to mitigate the vulnerability) CVE-2017-5754 [rogue data cache load] aka 'Meltdown' aka 'Variant 3' - Kernel supports Page Table Isolation (PTI): YES - PTI enabled and active: YES > STATUS: NOT VULNERABLE (PTI mitigates the vulnerability)
Don't see the difference? Look again in 'Hardware (CPU microcode) support for mitigation'. That's all, yes. Kind of sobering, I agree. Please blame Intel, not me.
Update: After reading this article, I understand that the microcode update only prepares the ground for the actual patch, which will come with kernel 4.15 and later versions. I'll check again then, of course after updating the 'Spectre & Meltdown Checker' (simply pulling the lastest version via 'git pull origin master').